
Database protection suite with field level encryption and intrusion detection.

| Perfect Acra-compatible applications | Typical industries |
|---|---|
| Web and mobile apps that store data in a centralised database or object storage |
|
| IoT apps that collect telemetry and process data in the cloud | |
| High-load data processing apps |

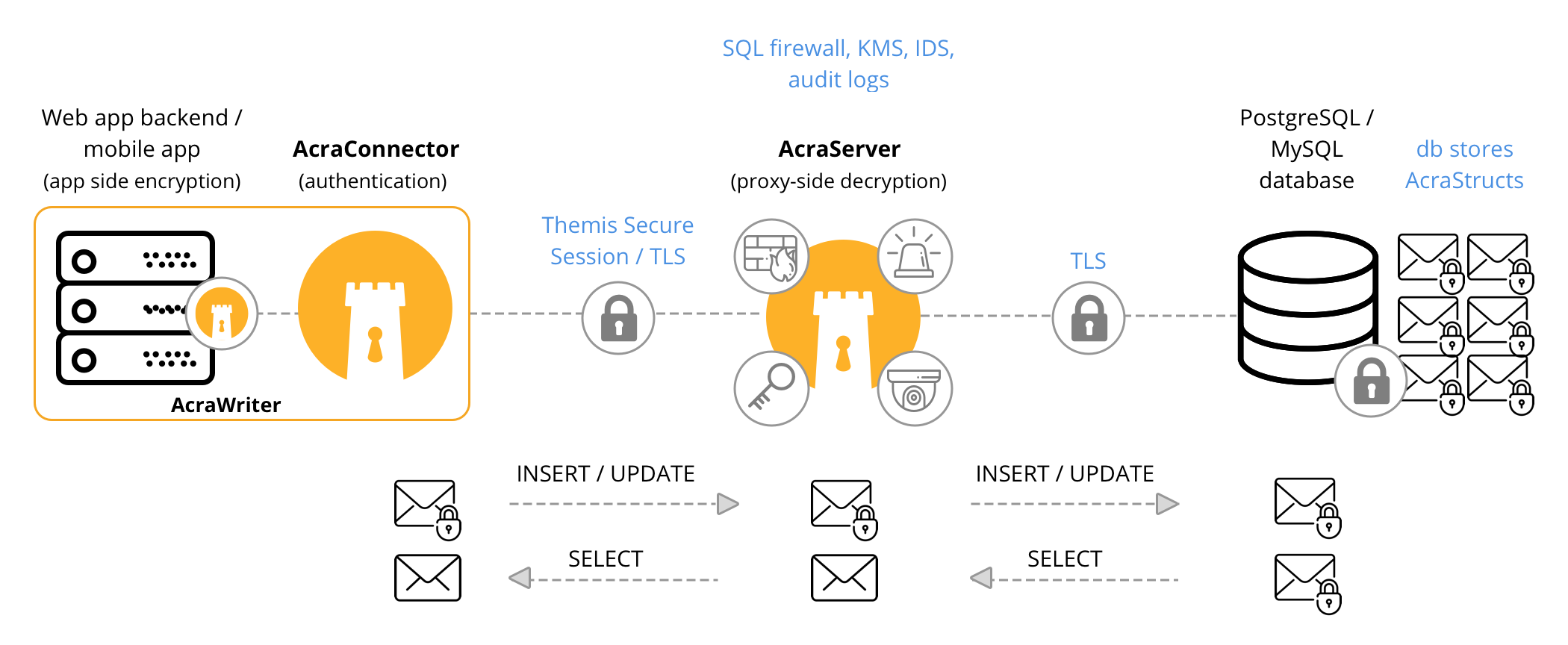
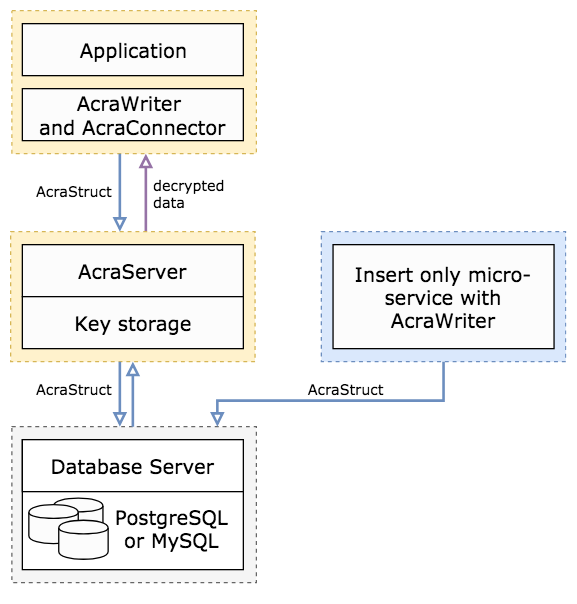
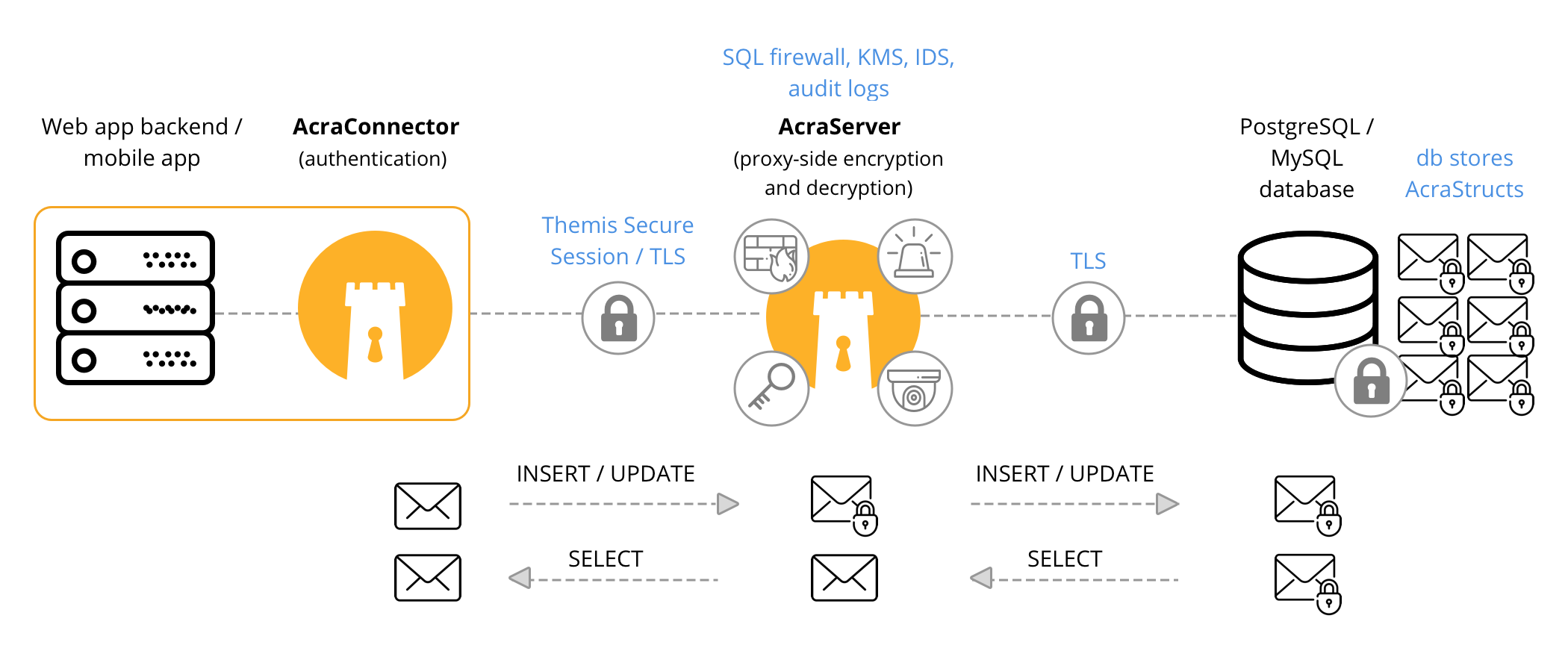
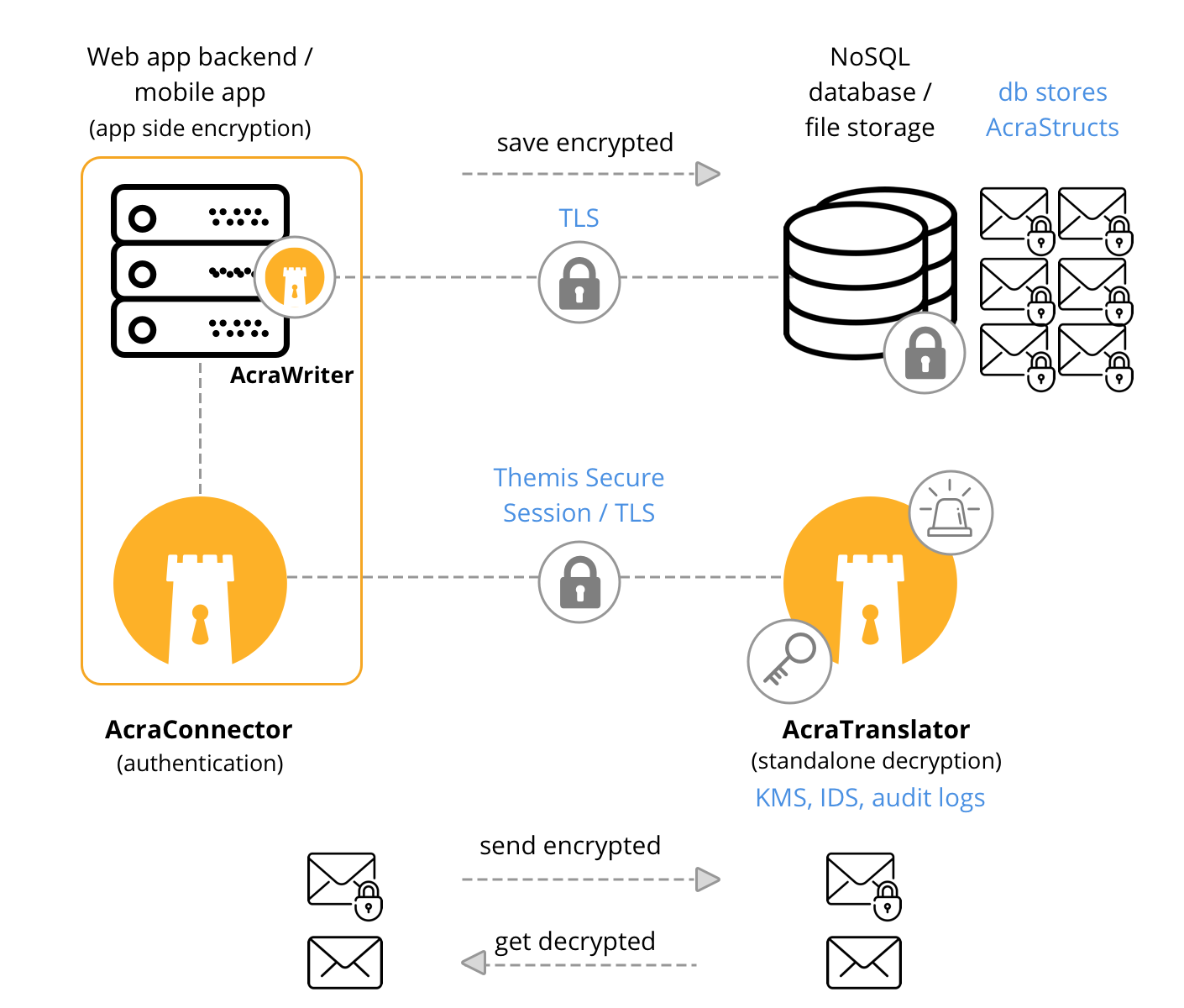
| field level encryption (client-side and/or proxy-side); each data record is encrypted using unique encryption keys |
|
| select which field/columns to encrypt to balance good security and performance | |
| built-in tools for key distribution, key rotation (with/without data re-encryption), and compartmentalisation | |
| datastore and application components can be compromised, yet the data stays protected | |
| through a built-in SQL firewall | |
| using poison records (honey tokens) to warn about suspicious behaviour | |
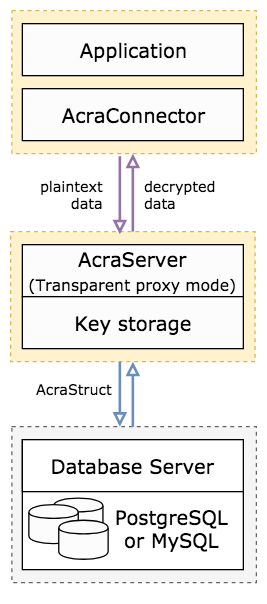
| encryption/decryption using AcraTranslator | |
| available for Acra Enterprise users | |
| your infrastructure is secure from the start without additional configuring | |
under the hood | no risk of selecting the wrong key length or algorithm padding |
| easy to configure and automate | |
| via binary packages or Docker images | |
| client-side encryption libraries support ~11 languages | |
| available for server-side encryption in AcraServer's Transparent proxy mode | |
| throughout all Acra components; compatible with ELK stack, Prometheus, Jaeger | |
| rollback utilities to decrypt database into plaintext | |
| numerous web-based and Docker-based example projects available | |
| run AcraServer in your DigitalOcean cloud | |
| we can setup and manage Acra for you |
| Default crypto-primitive source | OpenSSL |
| Supported crypto-primitive sources ᵉ | BoringSSL, LibreSSL, FIPS-compliant, GOST-compliant, HSM |
| Storage encryption | AES-256-GCM + ECDH |
| Transport encryption | TLS v1.2+ / Themis Secure Session |
| KMS integration ᵉ | Amazon KMS, Google Cloud Platform KMS, Hashicorp Vault, Keywhiz |
| Distributive | Instruction set | Download package | or alternatively |
|---|---|---|---|
| CentOS 7 | x86_64 | rpm package | use Docker or build from source |
| Debian Stretch (9) Debian Jessie (8) | x86_64/i386 | deb package | |
| Ubuntu Bionic (18.04) | x86_64 | deb package | |
| Ubuntu Artful (17.10) Ubuntu Xenial (16.04) | x86_64/i386 | deb package | |
| macOS (10.12 - 10.14) | x86_64 | - |
| Cloud platforms | DigitalOcean, AWS, GCP, Heroku |
| RDBMS | MySQL v5.7+, PosgtreSQL v9.4-v11, MariaDB v10.3 Google Cloud SQL, Amazon RDS |
| Object stores | filesystems, KV databases, Amazon S3, Google Cloud DataStore |
| Load balancing | HAProxy, cloud balancers |
 Developers and Ops friendly:
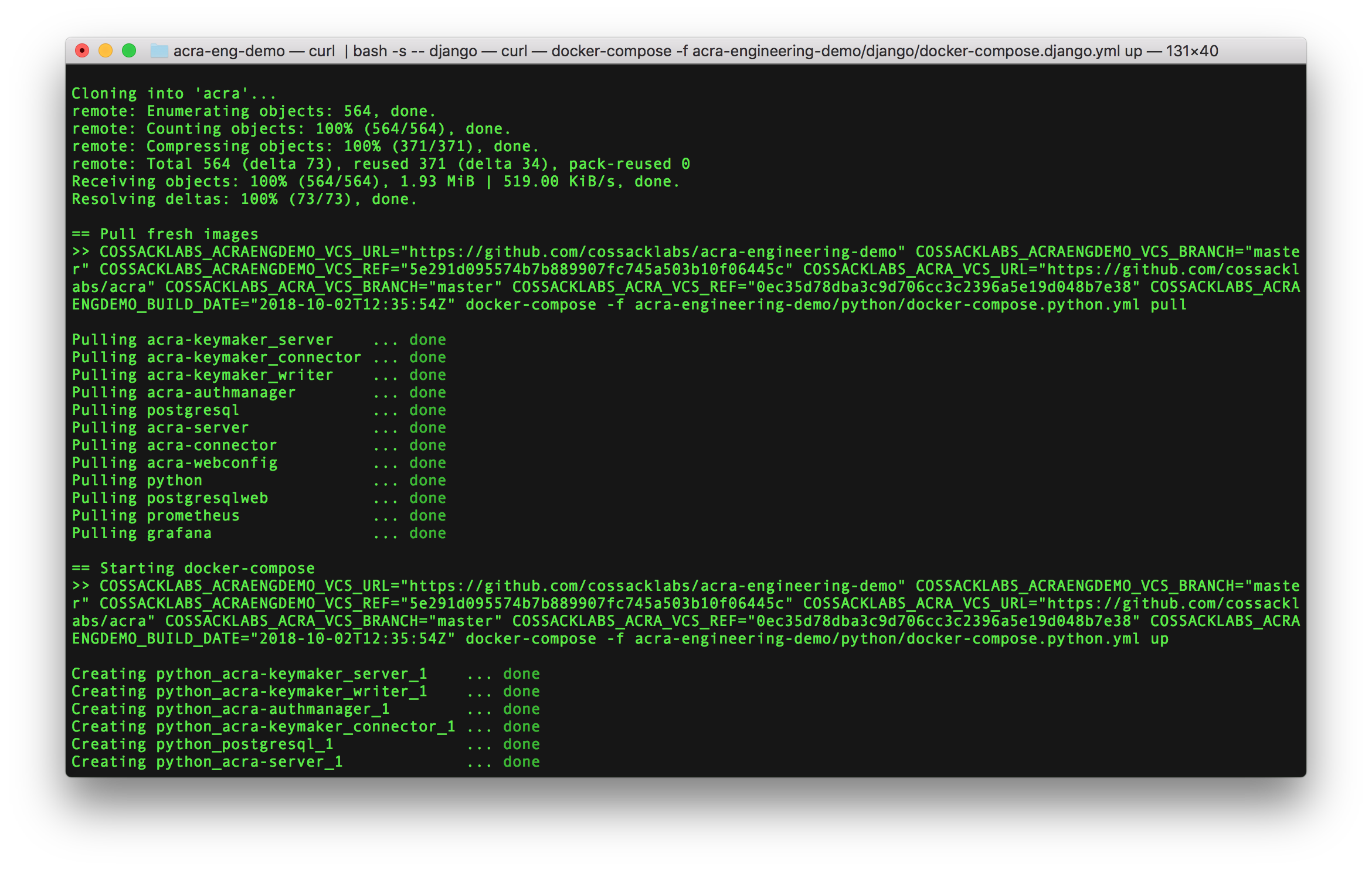
* run a single command to deploy the application, database, Acra's components, logs, and dashboards;
* read the code changes and see how little it takes to integrate encryption into the client application;
* learn how Acra works by reading logs, monitoring metrics in Prometheus, checking tracers in Jaeger and watching Grafana dashboards;
* inspect Docker-compose files, architecture schemes, database tables, and much more.
Requirements: Linux or macOS with installed Docker.
| ⚙️ [Run Acra Example Projects](https://github.com/cossacklabs/acra-engineering-demo) ⚙️ |
|---|
### Quick integration into your infrastructure
For a quick and easy integration of Acra into your own infrastructure, we recommend [trying Acra with Docker](http://docs.cossacklabs.com/pages/trying-acra-with-docker/) first. Using only two commands, you will get all the Acra's components and database up and running, with a secure transport layer between them. We prepared several typical infrastructure variants to experiment with.
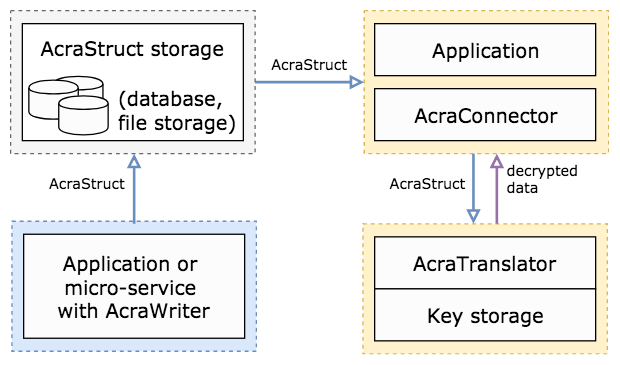
* Select one appropriate use case from the [pre-made configurations](https://docs.cossacklabs.com/pages/trying-acra-with-docker/) ("Compose files"): use AcraServer-based configuration to protect the data in a database or select AcraTranslator to protect the files or any other binary blob stored elsewhere.
* Launch Acra's server-side by running the selected Docker-compose file: it will generate the appropriate keys, put them into correct folders, perform a public key exchange, run selected services and database, and then it will listen to the incoming connections.
* Integrate [AcraWriter](https://docs.cossacklabs.com/pages/documentation-acra/#client-side-acraconnector-and-acrawriter) into your application code where you need to protect the sensitive data, supply AcraWriter with an Acra storage public key (generated by Docker-compose on the previous step). Encrypt the data into AcraStructs and send them into the database or file storage.
* Decrypt data by reading the database through AcraServer or by decrypting the files through AcraTranslator.
Please use the Acra Docker demo stand for testing/experimenting purposes only as the encryption keys are pre-generated in the configuration.
### Normal integration into your infrastructure
For production environments, we insist on generating and exchanging keys manually and deploying Acra as Docker containers or from source code. Refer to the [Quick Start guide](https://docs.cossacklabs.com/pages/documentation-acra/#installing-acra-from-the-cossack-labs-repository) to understand how to download and launch Acra components, generate keys, and perform the key exchange properly.
## Documentation, tutorials, additional information
The most recent versions of the documentation, tutorials, and demos for Acra are available on the official [Cossack Labs Documentation Server](https://docs.cossacklabs.com/products/acra/). The Github Wiki documentation is deprecated and is no longer updated since v0.82.0.
To gain an initial understanding of Acra, you might want to:
- Read about using the lightweight [HTTP web server AcraWebConfig](https://docs.cossacklabs.com/pages/documentation-acra/#acrawebconfig) we provide to manage AcraServer configuration in a simple fashion.
- Read the notes on [security design](https://docs.cossacklabs.com/pages/security-design/) and [intrusion detection](https://docs.cossacklabs.com/pages/intrusion-detection/) to better understand what you get when you use Acra and what is the threat model that Acra operates in.
- Key and trust management tools: [key distribution](https://docs.cossacklabs.com/pages/documentation-acra/#key-management), [key rotation](https://docs.cossacklabs.com/pages/acrarotate/) and [database rollback](https://docs.cossacklabs.com/pages/acrarollback/).
- Set up [rules for AcraCensor (SQL firewall)](https://doc-staging.dev.cossacklabs.com/pages/documentation-acra/#acracensor-acra-s-firewall) suitable for your application.
- Read [some notes on making Acra stronger, more productive, and efficient](https://docs.cossacklabs.com/pages/tuning-acra/) and about adding security features or increasing throughput, depending on your goals and security model.
- Read about the [logging format](https://docs.cossacklabs.com/pages/documentation-acra/#logging-in-acra) that Acra supports if you are using a SIEM system.
You can also check out the speaker slides for the following talks by Cossack Labs engineers:
- ["Encryption Without Magic, Risk Management Without Pain"](https://speakerdeck.com/vixentael/encryption-without-magic-risk-management-without-pain) by [Anastasiia Voitova](https://github.com/vixentael).
- ["Data encryption for Ruby web applications"](https://speakerdeck.com/shad/data-encryption-for-ruby-web-applications) by [Dmytro Shapovalov](https://github.com/shadinua).
- ["Building SQL firewall(AcraCensor): insights from developers"](https://speakerdeck.com/storojs72/building-sql-firewall-insights-from-developers) by [Artem Storozhuk](https://github.com/storojs72).
## Demo projects
| [Client-side encryption mode](https://github.com/cossacklabs/acra-engineering-demo/#examples-1-2-protecting-data-on-django-based-web-site) | [Transparent encryption mode](https://github.com/cossacklabs/acra-engineering-demo/#transparent-encryption-mode) |
| --- | --- |
### AcraCensor: SQL firewall to prevent SQL injections
[AcraCensor example application](https://github.com/cossacklabs/acra-engineering-demo/#example-6-sql-injections-prevention-with-acra) illustrates how to use [AcraCensor](https://docs.cossacklabs.com/pages/documentation-acra/#acracensor-acra-s-firewall) as SQL firewall to prevent SQL injections. The target application is a well-known vulnerable web application [OWASP Mutillidae 2](https://github.com/webpwnized/mutillidae).
The demo project has a Docker-compose file that runs the following web infrastructure:
- OWASP Mutillidae web application,
- Acra encryption suite.
Acra works as a proxy between web and database. AcraCensor inspects every SQL query that runs from the web application to the database, and back, and blocks suspicious queries.
Developers and Ops friendly:
* run a single command to deploy the application, database, Acra's components, logs, and dashboards;
* read the code changes and see how little it takes to integrate encryption into the client application;
* learn how Acra works by reading logs, monitoring metrics in Prometheus, checking tracers in Jaeger and watching Grafana dashboards;
* inspect Docker-compose files, architecture schemes, database tables, and much more.
Requirements: Linux or macOS with installed Docker.
| ⚙️ [Run Acra Example Projects](https://github.com/cossacklabs/acra-engineering-demo) ⚙️ |
|---|
### Quick integration into your infrastructure
For a quick and easy integration of Acra into your own infrastructure, we recommend [trying Acra with Docker](http://docs.cossacklabs.com/pages/trying-acra-with-docker/) first. Using only two commands, you will get all the Acra's components and database up and running, with a secure transport layer between them. We prepared several typical infrastructure variants to experiment with.
* Select one appropriate use case from the [pre-made configurations](https://docs.cossacklabs.com/pages/trying-acra-with-docker/) ("Compose files"): use AcraServer-based configuration to protect the data in a database or select AcraTranslator to protect the files or any other binary blob stored elsewhere.
* Launch Acra's server-side by running the selected Docker-compose file: it will generate the appropriate keys, put them into correct folders, perform a public key exchange, run selected services and database, and then it will listen to the incoming connections.
* Integrate [AcraWriter](https://docs.cossacklabs.com/pages/documentation-acra/#client-side-acraconnector-and-acrawriter) into your application code where you need to protect the sensitive data, supply AcraWriter with an Acra storage public key (generated by Docker-compose on the previous step). Encrypt the data into AcraStructs and send them into the database or file storage.
* Decrypt data by reading the database through AcraServer or by decrypting the files through AcraTranslator.
Please use the Acra Docker demo stand for testing/experimenting purposes only as the encryption keys are pre-generated in the configuration.
### Normal integration into your infrastructure
For production environments, we insist on generating and exchanging keys manually and deploying Acra as Docker containers or from source code. Refer to the [Quick Start guide](https://docs.cossacklabs.com/pages/documentation-acra/#installing-acra-from-the-cossack-labs-repository) to understand how to download and launch Acra components, generate keys, and perform the key exchange properly.
## Documentation, tutorials, additional information
The most recent versions of the documentation, tutorials, and demos for Acra are available on the official [Cossack Labs Documentation Server](https://docs.cossacklabs.com/products/acra/). The Github Wiki documentation is deprecated and is no longer updated since v0.82.0.
To gain an initial understanding of Acra, you might want to:
- Read about using the lightweight [HTTP web server AcraWebConfig](https://docs.cossacklabs.com/pages/documentation-acra/#acrawebconfig) we provide to manage AcraServer configuration in a simple fashion.
- Read the notes on [security design](https://docs.cossacklabs.com/pages/security-design/) and [intrusion detection](https://docs.cossacklabs.com/pages/intrusion-detection/) to better understand what you get when you use Acra and what is the threat model that Acra operates in.
- Key and trust management tools: [key distribution](https://docs.cossacklabs.com/pages/documentation-acra/#key-management), [key rotation](https://docs.cossacklabs.com/pages/acrarotate/) and [database rollback](https://docs.cossacklabs.com/pages/acrarollback/).
- Set up [rules for AcraCensor (SQL firewall)](https://doc-staging.dev.cossacklabs.com/pages/documentation-acra/#acracensor-acra-s-firewall) suitable for your application.
- Read [some notes on making Acra stronger, more productive, and efficient](https://docs.cossacklabs.com/pages/tuning-acra/) and about adding security features or increasing throughput, depending on your goals and security model.
- Read about the [logging format](https://docs.cossacklabs.com/pages/documentation-acra/#logging-in-acra) that Acra supports if you are using a SIEM system.
You can also check out the speaker slides for the following talks by Cossack Labs engineers:
- ["Encryption Without Magic, Risk Management Without Pain"](https://speakerdeck.com/vixentael/encryption-without-magic-risk-management-without-pain) by [Anastasiia Voitova](https://github.com/vixentael).
- ["Data encryption for Ruby web applications"](https://speakerdeck.com/shad/data-encryption-for-ruby-web-applications) by [Dmytro Shapovalov](https://github.com/shadinua).
- ["Building SQL firewall(AcraCensor): insights from developers"](https://speakerdeck.com/storojs72/building-sql-firewall-insights-from-developers) by [Artem Storozhuk](https://github.com/storojs72).
## Demo projects
| [Client-side encryption mode](https://github.com/cossacklabs/acra-engineering-demo/#examples-1-2-protecting-data-on-django-based-web-site) | [Transparent encryption mode](https://github.com/cossacklabs/acra-engineering-demo/#transparent-encryption-mode) |
| --- | --- |
### AcraCensor: SQL firewall to prevent SQL injections
[AcraCensor example application](https://github.com/cossacklabs/acra-engineering-demo/#example-6-sql-injections-prevention-with-acra) illustrates how to use [AcraCensor](https://docs.cossacklabs.com/pages/documentation-acra/#acracensor-acra-s-firewall) as SQL firewall to prevent SQL injections. The target application is a well-known vulnerable web application [OWASP Mutillidae 2](https://github.com/webpwnized/mutillidae).
The demo project has a Docker-compose file that runs the following web infrastructure:
- OWASP Mutillidae web application,
- Acra encryption suite.
Acra works as a proxy between web and database. AcraCensor inspects every SQL query that runs from the web application to the database, and back, and blocks suspicious queries.
 Requirements: Linux or macOS with installed Docker.
| ⚙️ [Run AcraCensor SQL firewall example](https://github.com/cossacklabs/acra-engineering-demo/#example-6-sql-injections-prevention-with-acra) ⚙️ |
|---|
### Poison records: intrusion detection example
[Intrusion detection example application](https://github.com/cossacklabs/acra-engineering-demo/#example-7-intrusion-detection-with-acra) illustrates how to use poison records (honey tokens) as "intrusion markers" that warn about possible attack.
Requirements: Linux or macOS with installed Docker.
| 🍯 [Run intrusion detection example](https://github.com/cossacklabs/acra-engineering-demo/#example-7-intrusion-detection-with-acra) 🐝 |
|---|
### Acra Load Balancing Example
[Acra load balancing example application](https://github.com/cossacklabs/acra-engineering-demo/#example-8-load-balancing-with-acra) illustrates building high availability and balanced infrastructure, based on Acra components, PostgreSQL, and Python web application. We prepared several configurations with multiple databases and HAProxy.
| 🔛 [Run Acra Load Balancing Example](https://github.com/cossacklabs/acra-engineering-demo/#example-8-load-balancing-with-acra) 🔛 |
|---|
## GDPR, HIPAA, CCPA
Acra can help you comply with the current privacy regulations, such as:
* [General Data Protection Regulation (GDPR)](https://gdpr-info.eu/)
* [HIPAA (Health Insurance Portability and Accountability Act)](https://en.wikipedia.org/wiki/Health_Insurance_Portability_and_Accountability_Act)
* [DPA (Data Protection Act)](http://www.legislation.gov.uk/ukpga/2018/12/contents/enacted)
* [CCPA (California Consumer Privacy Act)](https://en.wikipedia.org/wiki/California_Consumer_Privacy_Act)
Configuring and using Acra in a designated form will cover most of the demands described in articles 25, 32, 33, and 34 of GDPR and the PII data protection demands of HIPAA. Read more about [Acra and GDPR compliance here](http://docs.cossacklabs.com/pages/acra-and-gdpr-compliance/).
## Open source vs Pro vs Enterprise
This is Acra Community Edition, the open source version of Acra, which is 💯 free for commercial and non-commercial usage. Please let us know in the [Issues](https://www.github.com/cossacklabs/acra/issues) if you stumble upon a bug, see a possible enhancement, or have a comment on security design.
There are also [Pro and Enterprise versions of Acra](https://www.cossacklabs.com/acra/#pricing) available. Those versions provide better performance, redundancy/load balancing, come pre-configured with crypto-primitives of your choice (FIPS, GOST), have integration with key/secret management tools in your stack, provide unique security features like search through encrypted data, and have plenty of utils and tools for your Ops and SREs to operate Acra conveniently – deployment automation, scaling, monitoring, and logging. [Talk to us](mailto:sales@cossacklabs.com) to get full feature lists and a quote.
## Security consulting
It takes more than just getting cryptographic code to compile to secure the sensitive data. Acra won't make you “compliant out of the box” with all the modern security regulations, and no other tool will.
[We help companies](https://www.cossacklabs.com/services/overview/) plan their data security strategy by auditing, assessing data flow, and classifying the data, enumerating the risks. We do the hardest, least-attended part of reaching the compliance – turning it from the “cost of doing business” into the “security framework that prevents risks”.
## Contributing to us
If you’d like to contribute your code or provide any other kind of input to Acra, you’re very welcome. Your starting point for contributing [is here](https://docs.cossacklabs.com/pages/documentation-acra/#contributing-to-acra).
## License
Acra is licensed as Apache 2 open-source software.
## Contacts
If you want to ask a technical question, feel free to raise an [Issue](https://github.com/cossacklabs/acra/issues) or write to [dev@cossacklabs.com](mailto:dev@cossacklabs.com).
To talk to the business wing of Cossack Labs Limited, drop us an email to [info@cossacklabs.com](mailto:info@cossacklabs.com).
[](https://cossacklabs.com/) [](https://twitter.com/cossacklabs) [](https://medium.com/@cossacklabs/)
Requirements: Linux or macOS with installed Docker.
| ⚙️ [Run AcraCensor SQL firewall example](https://github.com/cossacklabs/acra-engineering-demo/#example-6-sql-injections-prevention-with-acra) ⚙️ |
|---|
### Poison records: intrusion detection example
[Intrusion detection example application](https://github.com/cossacklabs/acra-engineering-demo/#example-7-intrusion-detection-with-acra) illustrates how to use poison records (honey tokens) as "intrusion markers" that warn about possible attack.
Requirements: Linux or macOS with installed Docker.
| 🍯 [Run intrusion detection example](https://github.com/cossacklabs/acra-engineering-demo/#example-7-intrusion-detection-with-acra) 🐝 |
|---|
### Acra Load Balancing Example
[Acra load balancing example application](https://github.com/cossacklabs/acra-engineering-demo/#example-8-load-balancing-with-acra) illustrates building high availability and balanced infrastructure, based on Acra components, PostgreSQL, and Python web application. We prepared several configurations with multiple databases and HAProxy.
| 🔛 [Run Acra Load Balancing Example](https://github.com/cossacklabs/acra-engineering-demo/#example-8-load-balancing-with-acra) 🔛 |
|---|
## GDPR, HIPAA, CCPA
Acra can help you comply with the current privacy regulations, such as:
* [General Data Protection Regulation (GDPR)](https://gdpr-info.eu/)
* [HIPAA (Health Insurance Portability and Accountability Act)](https://en.wikipedia.org/wiki/Health_Insurance_Portability_and_Accountability_Act)
* [DPA (Data Protection Act)](http://www.legislation.gov.uk/ukpga/2018/12/contents/enacted)
* [CCPA (California Consumer Privacy Act)](https://en.wikipedia.org/wiki/California_Consumer_Privacy_Act)
Configuring and using Acra in a designated form will cover most of the demands described in articles 25, 32, 33, and 34 of GDPR and the PII data protection demands of HIPAA. Read more about [Acra and GDPR compliance here](http://docs.cossacklabs.com/pages/acra-and-gdpr-compliance/).
## Open source vs Pro vs Enterprise
This is Acra Community Edition, the open source version of Acra, which is 💯 free for commercial and non-commercial usage. Please let us know in the [Issues](https://www.github.com/cossacklabs/acra/issues) if you stumble upon a bug, see a possible enhancement, or have a comment on security design.
There are also [Pro and Enterprise versions of Acra](https://www.cossacklabs.com/acra/#pricing) available. Those versions provide better performance, redundancy/load balancing, come pre-configured with crypto-primitives of your choice (FIPS, GOST), have integration with key/secret management tools in your stack, provide unique security features like search through encrypted data, and have plenty of utils and tools for your Ops and SREs to operate Acra conveniently – deployment automation, scaling, monitoring, and logging. [Talk to us](mailto:sales@cossacklabs.com) to get full feature lists and a quote.
## Security consulting
It takes more than just getting cryptographic code to compile to secure the sensitive data. Acra won't make you “compliant out of the box” with all the modern security regulations, and no other tool will.
[We help companies](https://www.cossacklabs.com/services/overview/) plan their data security strategy by auditing, assessing data flow, and classifying the data, enumerating the risks. We do the hardest, least-attended part of reaching the compliance – turning it from the “cost of doing business” into the “security framework that prevents risks”.
## Contributing to us
If you’d like to contribute your code or provide any other kind of input to Acra, you’re very welcome. Your starting point for contributing [is here](https://docs.cossacklabs.com/pages/documentation-acra/#contributing-to-acra).
## License
Acra is licensed as Apache 2 open-source software.
## Contacts
If you want to ask a technical question, feel free to raise an [Issue](https://github.com/cossacklabs/acra/issues) or write to [dev@cossacklabs.com](mailto:dev@cossacklabs.com).
To talk to the business wing of Cossack Labs Limited, drop us an email to [info@cossacklabs.com](mailto:info@cossacklabs.com).
[](https://cossacklabs.com/) [](https://twitter.com/cossacklabs) [](https://medium.com/@cossacklabs/)